Unlocking Sensitive Data: 10 Google Dorks You Need to Know
Written on
Chapter 1: Introduction to Google Dorks
In the realm of cybersecurity, Google Dorks are invaluable tools that help uncover sensitive information inadvertently exposed on the internet. By utilizing specific search queries, you can discover hidden documents and data across various platforms. Below, we delve into ten Google Dorks that can aid in locating sensitive data.

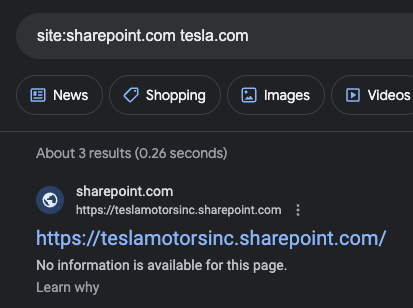
Section 1.2: OneDrive - Discover Internal Presentations
OneDrive is a widely used cloud storage service. You can uncover internal presentations and private images that may have been mistakenly shared publicly using this query:
site:onedrive.live.com "example.com"
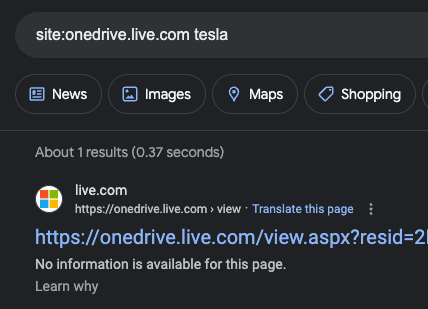
Section 1.3: Dropbox - Accessing Critical Data
Utilize the following search to expose Dropbox links that might contain source code or proprietary information:
site:dropbox.com/s "example.com"
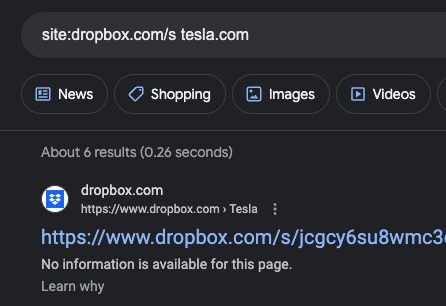
Section 1.4: Box - Finding Sensitive Contracts
Search for potentially sensitive files on Box using this query:
site:box.com/s "example.com"
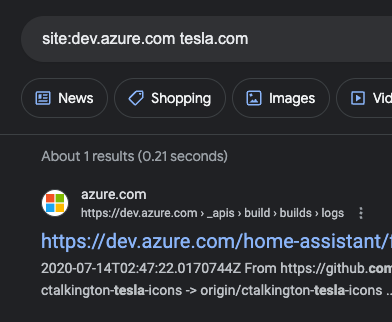
Section 1.5: Azure DevOps - Exposing API Keys
With Microsoft’s Azure DevOps, you can discover critical information like unsecured repositories and API keys by using:
site:dev.azure.com "example.com"
Chapter 2: More Google Dorks for Cybersecurity
The video titled "HakByte: How to find anything on the internet with Google Dorks" provides in-depth insights into effectively using Google Dorks for your cybersecurity efforts.
Check out the video "Top 7 Google Dorks of 2023 (Google HACKING)" to learn about the most effective Google Dorks currently in use for cybersecurity.
Section 2.3: Firebase - Exposing Application Secrets
Search Firebase-hosted files to discover app secrets and user data:
site:firebaseio.com "example"
Section 2.4: JFrog - Identifying Security Risks
Find exposed artifacts and builds on JFrog by using:
site:jfrog.io "example"
Section 2.5: Amazon S3 - Accessing Sensitive Data
To uncover sensitive files in lesser-known S3 subdomains, try the following searches:
site:http://s3-external-1.amazonaws.com "example.com"
site:http://s3.dualstack.us-east-1.amazonaws.com "example.com"
With these powerful search strings at your disposal, you'll be well-equipped to discover hidden information across the internet.
For more on Google Dorks and their applications, follow these resources:
- Reveal the Cloud with Google Dorks: Find sensitive data in Amazon AWS, Google Cloud, and more: infosecwriteups.com
- 5 Google Dorks Every Hacker Should Know: Discover hidden endpoints and sensitive data: thegrayarea.tech
- GitHub Resources:
— Mike Takahashi