Understanding DLL Hijacking: A Deep Dive into Cybersecurity
Written on
Chapter 1: Introduction to DLL Hijacking
Imagine a situation where your organization faces a significant data breach, prompting a temporary network shutdown. After implementing new firewall rules and adjusting your intrusion detection systems, you might believe the attackers have been successfully expelled. But is that truly the case? Or are you merely underestimating their persistence?
Once inside, an attacker will take deliberate steps to ensure they maintain access to the network. This persistence can lead to automatic reconnection to the compromised systems, regardless of the initial disconnection. Understanding this post-exploitation tactic is essential for cybersecurity.
Some common techniques attackers employ include:
- Extracting password hashes to gain system credentials and access other machines.
- Searching for stored credentials on various systems to facilitate further breaches.
- Manipulating the Windows registry to maintain control.
- Scheduling tasks that connect back to the attacker's machine, akin to cron jobs in Linux.
- Installing malicious applications that initiate connections on system startup.
With these methods, a technically savvy user may detect anomalies and begin investigating potential breaches. So, what remains for the attacker if these measures are compromised? If they can't execute code or sustain their presence, they must resort to alternative methods.
This leads us to the topic of DLL Hijacking, a technique that attackers leverage to ensure their code executes unnoticed. In this article, we will explore what DLLs are, the nature of DLL hijacking, and witness a practical demonstration of these concepts.
Chapter 2: What is a DLL?
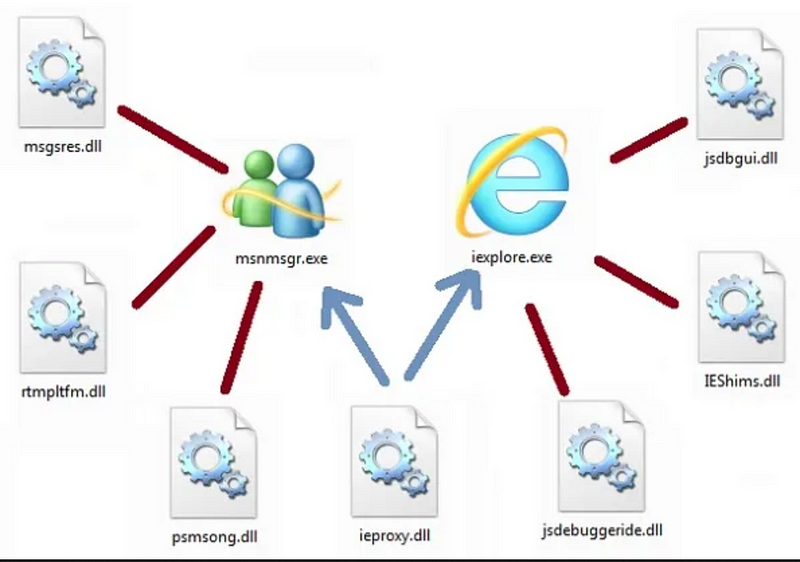
A Dynamic Link Library, or DLL, is a file type with a .dll extension that functions similarly to an executable, though it cannot be executed directly. Why are DLLs necessary?
They serve as public libraries that multiple applications can utilize for shared tasks. For instance, instead of rewriting code for a pop-up box in several applications, developers can import a single DLL to streamline the process. This modularity not only reduces redundancy but also enhances code reliability.
What is PATH?
How does an executable locate the required DLL? The answer lies in the PATH variable, which directs the operating system to the necessary file locations. This variable acts like your home address, guiding the OS to find commands when executed. If a command isn't in the current directory, the OS consults the PATH variable to locate it.
To print the PATH variable in Windows:
echo %PATH%
In Linux/MacOS:
echo $PATH
Understanding the Execution Flow
Consider an executable file named listfiles.exe located on the Desktop that relies on list.dll. If the DLL isn't found in the same directory, the operating system will check the directories listed in the PATH variable. If located, the DLL will execute; otherwise, an error message appears.
Demonstration of DLL Usage
Let's apply our understanding by creating an executable that loads a DLL. We'll use two files written in C. The first executable checks for a malicious DLL, as outlined in the following code snippet:
#include <stdio.h>
#include <windows.h>
int main() {
HMODULE hModule = LoadLibrary("malicious.dll");
if (hModule) {
printf("DLL Found & Executingn");} else {
printf("Errorn");}
return 0;
}
The second file is the malicious DLL:
#include <windows.h>
__declspec(dllexport) int ShowMessage() {
MessageBox(NULL, "DLL Hijacked", "Hacked", MB_ICONERROR | MB_OK);
return 0;
}
When executed, this DLL will display a message box indicating that the DLL has been hijacked.
Now, we will compile these files using the cross-compiler x86_64-w64-mingw32-gcc. To install it on Linux distributions, use:
sudo apt-get install gcc-mingw-w64
or
yum install gcc-mingw-w64
To generate the executable files, run:
x86_64-w64-mingw32-gcc loaddll.c -o loaddll.exe
x86_64-w64-mingw32-gcc malicious.c -o malicious.dll -shared
Next, transfer these files to a Windows machine. If you only run loaddll.exe, you will see an error because malicious.dll is missing. Once you copy the DLL and execute the loader again, the message "DLL Hijacked" will appear.
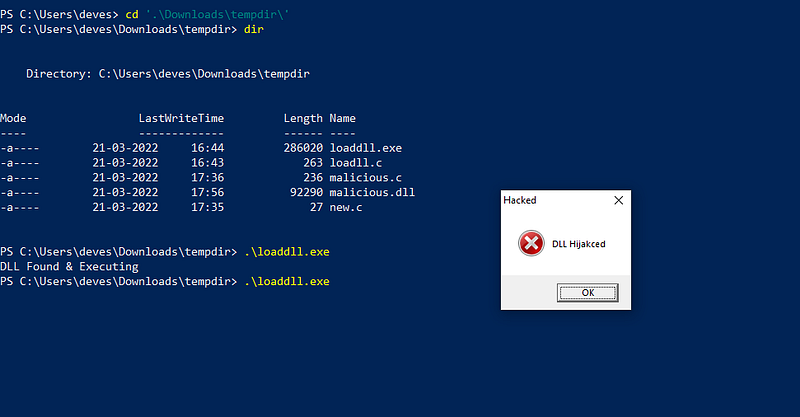
Note: You may need to disable Windows Defender for this demonstration. Various techniques exist to bypass its detection, but detailing them would complicate the discussion.
Conclusion
DLL Hijacking allows an attacker to exploit your computer's DLL files to run unauthorized code. If an attacker manages to place a malicious file on your system—via social engineering or other means—this file can execute when a vulnerable application is launched. It's crucial to scan files and employ antivirus solutions to mitigate such risks.
Chapter 3: Additional Resources
All About DLL Hijacking - My Favorite Persistence Method - This video delves into the nuances of DLL hijacking and its implications in cybersecurity.
DLL Hijacking - Hacking Attack Tutorial - A tutorial on executing DLL hijacking techniques and understanding their impact.